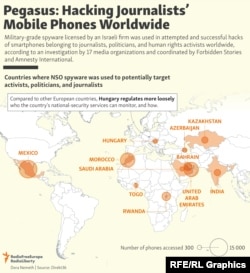
Spyware might seem like a key opportunity for governments in former Soviet republics focused on tracking media critical of their rule.
But out of Current Time’s coverage zone, only two countries, Azerbaijan and Kazakhstan, feature prominently in the findings of the Pegasus investigation published on July 18 by Forbidden Stories, a French non-profit that works with persecuted journalists, and human rights defender Amnesty International along with 17 partner media organizations.
Ukraine was identified as the location of four of the 425 servers allegedly used to host Pegasus “infection domains,” sites used to install the spyware on designated mobile devices.
The findings are based on a supposed Pegasus database leak of 50,000 cell phone numbers from over 50 countries provided to the Forbidden Stories-Amnesty International team by an unidentified source. Journalists account for “at least 180” of these numbers, Forbidden Stories reported.
The highest number of identified potential Pegasus targets was reported in Azerbaijan, where journalists made up most of the list of 80 such targets. Overall, the investigating team pinpointed more than 1,000 Azerbaijani phone numbers in the database leak.
Citing “contractual and national security considerations,” Pegasus’ vendor, the Herzliya, Israel-based NSO Group, has not confirmed or denied that any government is or has been among its clients, however. The private company, founded by veterans of the Israeli armed forces’ Unit 8222, a signals intelligence group, maintains that the malware, which can take control of a mobile device’s photos, contacts, message, and more, is sold to governments only for fighting terrorism and crime.
The Israeli Defense Ministry licenses the sales, which, as of 2016, could bring in at least $1.15 million each, according to a New York Times investigation of NSO Group.
At the time of the report, installation of Pegasus spyware cost a flat $500,000, the Times reported, citing a company proposal and other corporate documents.
Usage fees depended on the number of desired targets and their type of mobile device. Targeting iPhone or Android users cost $650,000 for 10 targets. Adding an additional 10 to 100 targets ranged from $150,000 to $800,000.
Clients also paid a yearly “system maintenance fee” that amounted to 17 percent of the total account fee, according to the Times.
Such costs tend to eliminate countries without hefty budgets for law enforcement or security services, observers say.
For Azerbaijan and Kazakhstan, both mega-energy exporters, however, Pegasus’ reported price tag likely would pose no obstacle.
Both countries are sizable oil exporters to Israel and have long-term relationships with the Israeli armed forces that include the purchase (Azerbaijan and Kazakhstan) or co-production (Kazakhstan) of Israeli drones. They also both have spotty freedom of speech records that include the targeting of opposition-linked or independent press, media rights activists charge.
Both the Azerbaijani and Kazakh governments, however, categorically deny that they use the Pegasus spyware or have targeted opponents and media with it.
AZERBAIJAN:
Out of the 10 countries tagged for the alleged use of Pegasus against potential targets, Azerbaijan, the wealthiest state in the South Caucasus, tops the list with 80 such individuals – nearly double the number of second-place Mexico, where investigators identified 43 potential targets.
Journalists accounted for roughly 53 percent of the 80 potential Azerbaijani targets named in the investigation.
One of these possible victims, award-winning Azerbaijani investigative journalist Khadija Ismayilova, a former Baku bureau chief for Radio Free Europe/Radio Liberty’s Azerbaijani Service, noted that the government listening into phone calls is “routine” in Azerbaijan. But spyware is not essential for this task.
Ismayilova never suspected that Pegasus was tracking her activities via her 2014 iPhone 6.
Ismayilova and other independent Azerbaijani journalists have used the messaging app Signal, known for its advanced encryption, to protect against government snooping. They believed that iPhones were safe to use “because the iOS is stronger than an Android’s,” Ismayilova remarked.
“But for this program (Pegasus), this doesn’t mean anything,” she added.
While newer phones are more difficult for spyware to hack, to Pegasus, “it doesn't matter if your phone is old or new,” noted Bill Marczak, a senior research fellow at Citizen Lab, a cybersecurity research project at the University of Toronto’s Munk School of Global Affairs & Public Policy that previously has investigated Pegasus spyware.
“The attacker sends an invisible iMessage to the target that contains a malicious attachment designed to exploit a flaw in the phone,” Marczak explained. “When the target's phone parses the attachment, this causes the phone to be hacked, and Pegasus to be installed.”
Marczak stated that Citizen Lab is familiar with at least 130 cases when the Pegasus program was used illegally; 50 of these incidents were cyberattacks against journalists, he said.
Ismayilova, who works for the international investigative journalism outlet OCCRP, a Pegasus investigation partner, learned that she may have been targeted only when she met this May with three OCCRP editors who showed her that her cell phone number had appeared in the leak from the Pegasus database.
She believes that the Azerbaijani authorities need journalists’ personal data to blackmail them and to incite “hatred.”
“In 2012, they physically placed a camera in my bedroom, the bathroom, and in the living room,” Ismayilova recounted. “And then this footage was used for blackmail, and when I refused and published the threats, all of this [footage] was placed on the Internet.”
The journalist had investigated rampant corruption among the higher ranks of power in Azerbaijan, including in President Ilham Aliyev’s family.
In 2015, Ismayilova was sentenced to 7 ½ years in prison – later reduced to 3 ½ -- on charges of alleged embezzlement and tax violations. Her lawyers, civil rights activists, and members of the international community insisted that the charges were politically motivated.
Ismayilova was released in 2016, but not allowed to leave the country until 2021.
Including Ismayilova, five current or former RFE/RL journalists covering Azerbaijan feature among the spyware’s potential victims, according to the investigation.(Current Time is led by RFE/RL in cooperation with Voice of America.)
"It is outrageous that in the 21st century, so many governments seek to block free expression and prevent journalists from providing objective news and information to their fellow citizens," RFE/RL President and Chief Executive Officer Jamie Fly said in a July 19 statement.
Fly urged the Azerbaijani government “to stop blocking our website, halt its surveillance of our staff and to cease its harassment of our former bureau chief Khadija Ismayilova.” (RFE/RL's Baku bureau closed in 2014.)
Phone numbers for other prominent journalists, including Mehman Aliyev, editor-in-chief of the country’s lone independent news agency, Turan, and reporters at former opposition-linked outlets, also featured in the database leak.
A spokesman for the Azerbaijani Interior Ministry, however, commented to RFE/RL’s Azerbaijani Service that claims that Baku had used the Israeli spyware to track government critics are “nonsense” and cannot be corroborated.
But the investigation found that Pegasus was used against pro-government Azerbaijani journalists as well.
The Azerbaijani TV station Real TV periodically shows intimate recordings of critics of the Azerbaijani authorities. The phone number of its founder, journalist Mir Shahin Agayev, also featured among the Azerbaijani numbers contained in the Pegasus database leak.
Real TV did not respond to a Current Time request for a response.
Another prominent journalist, Eynulla Fatullayev, a former internationally recognized political prisoner now often seen as sympathetic to the authorities, has not commented on his inclusion in the list.
Azerbaijan Journalists’ Union Chairman Elchin Shikhly, awarded by President Ilham Aliyev in 2020 for “service to the motherland,” also was listed among the potential targets.
In response to these revelations, some Azerbaijani journalists intend to fight back.
Reporter Sevinc Vaqifqizi, who works for the Berlin-based Azerbaijani news outlet Meydan TV, told the Committee to Protect Journalists that independent journalists intend to take the Azerbaijani government to court over its alleged infiltration of their cell phones.
“My colleagues and I will keep working,” Vaqifqizi said. “I know that the government will continue surveilling us, but they won’t stop us. “
BELARUS & RUSSIA
Two countries routinely charged with systematically tracking, prosecuting, detaining, or arresting journalists who challenge the government -- Belarus and Russia -- were not included in the list of alleged Pegasus users.
Though Belarus gives critical journalists short shrift, using Pegasus could be prohibitively expensive, given the country’s ongoing financial difficulties.
In Russia, one of the world’s most frequently cited sources of cyberattacks, two factors likely blocked any government interest in Pegasus, according to a specialist in Russian intelligence agencies.
“On the world market for espionage technology, Russia is a seller, not a buyer,” Russian investigative journalist Andrei Soldatov wrote in a July 21 op-ed for The Moscow Times.
Additionally, the Federal Security Service, Russia’s domestic intelligence agency, is “extremely paranoid about foreign spyware,” Soldatov continued, since it fears that the technology could make it vulnerable to penetration by the intelligence service of the spyware vendor’s home country; in this case, Israel.
Amnesty International’s list of Pegasus-related domains, though, includes several Russian-language addresses, now all disabled: oplata-shtraf.info, photo-afisha.net, mystulchik.com, prikol-girls.com, and sputnik-news.info.
The last domain name, sputnik-news.info, resembles that of the state-run Russian news agency Sputnik (https://sputniknews.com/).
A connection between these domains and Russia has not been identified. Russia does not feature among the 16 countries whose servers were used for Pegasus infection domains, according to Amnesty International.
KAZAKHSTAN:
In Kazakhstan, another wealthy energy giant with a muddied civil rights record, around 2,000 phone numbers, including those for members of the country’s business and political elite, were contained in the Pegasus database leak.
Among the 11 individuals identified as potential targets, only two are journalists.
If his status as a Pegasus target is confirmed, journalist Serikzhan Mauletbay, who also advocates for improved freedom of expression in Kazakhstan, plans to file an official complaint with Kazakh prosecutors for the government violating his constitutional rights.
“I don’t know what they didn’t like about my activities, but I’m an active journalist, often putting inconvenient questions to officials, and raising controversial topics that our civil servants would not like to see in the public arena,” Mauletbay commented to Current Time Asia on July 21.
Bigeldy Gabdullin, a longtime journalist with a track record of court clashes with the government after publishing criticism of their activities, also features among Pegasus’ potential targets, according to the investigation.
The inclusion of Kazakh President Kassym-Jomart Tokaev and Prime Minister Askar Mamin also on this list made headlines, but the first deputy head of the presidential administration has recommended “sensible skepticism” toward the Pegasus report.
“[A]nyone can be included in this list and, thus, sow seeds of doubt in the country among the elite, among journalists, and so on,” Dauren Abayev commented during a July 22 TV interview with the state-run Khabar channel.
UKRAINE & LITHUANIA:
With a middling ranking for freedom of speech from the watchdog Reporters Without Borders, Ukraine does not feature in the Pegasus investigation’s list of potentially targeted phone numbers.
But the country, a frequent target of cyberattacks, does contain four of the servers reportedly used to host the so-called “infection domains” used in Pegasus’ attacks on mobile devices, according to Amnesty International.
Kyiv Optic Networks, Ltd. (KievNet), one of the country’s largest Internet Service Providers, and PE Brezhnev Daniil each hosted one of the domains. The latter server has the same name as Daniil Brezhnev, owner of the anonymous hosting service NetEngi, based in the central Ukrainian city of Dnipro.
Virtual Systems, LLC, based in Kyiv, is a roughly 12-year-old anonymous hosting service with servers in both the Ukrainian capital and Amsterdam, The Netherlands. Amnesty International identified it as the host of two servers related to the Pegasus attacks.
In Ukraine’s near neighbor Lithuania, only one hosting company, UAB Rakrejus, was named as allegedly providing a server for Pegasus-related domains.
Amnesty International has not identified the addresses of the domains supposedly located on any of these servers.
The server hosts named do not appear to have responded publicly to the Pegasus report.
WHO'S LIABLE?
Most countries’ laws forbid the use of spyware like Pegasus if “knowingly created with an illegal aim,” commented Vladimir Ozherelyev, an expert with Russia’s non-governmental digital rights organization Roskomsvoboda.
That condition, though, means that Pegasus’ developers might not be held liable for violating victims’ rights, Ozherelyev commented.
“Nonetheless, individuals who knowingly use the program illegally, including those who use their official position [to do so], can be held responsible,” he added.
Ozherelyev also does not exclude that, in certain cases, cyberattack victims can receive compensation in national and international courts.
Contacted by Current Time, a spokesman for NSO Group replied with the company’s previously released statement that it is considering a defamation lawsuit. The company termed the claim of a database leak “a complete lie and ridiculous, since the data never existed on any of our servers.”
It emphasized that the company “does not operate the system” that client governments run to use Pegasus and does not have “visibility to the data.”
NSO Group claims that, in the past, it has disabled client accounts for making improper use of Pegasus.
It describes itself as on a “life-saving mission” to “prevent terror attacks, gun violence, car explosions and suicide bombings” as well as to “break up” rings of drug-traffickers and sexual abusers, among other endeavors.
Nonetheless, the Forbidden Stories-Amnesty International team has pledged that its investigation into Pegasus will continue.