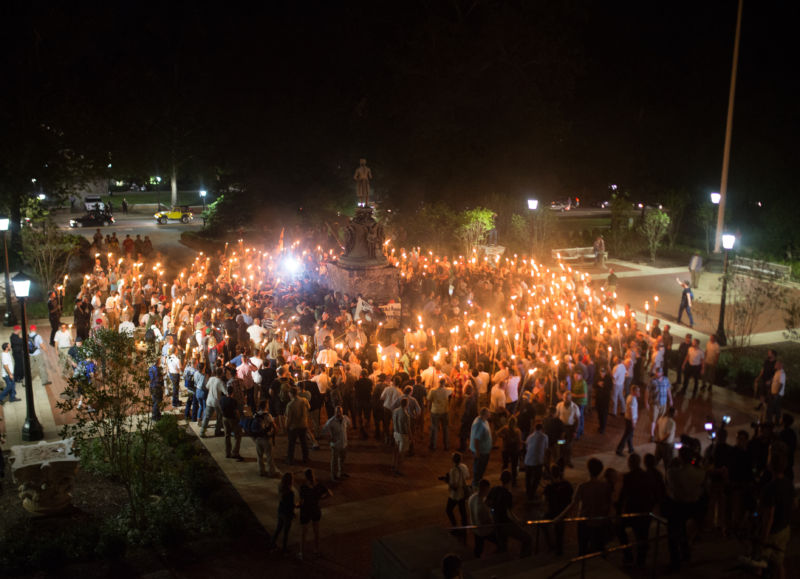
In the wake of last week's "Unite the Right" march in Charlottesville, Virginia—as well as the vehicular murder of a woman by (probably) a neo-Nazi connected to the event—the quest to identify and out those who marched with white supremacist and neo-Nazi groups last Friday and Saturday is in full swing.
In short order, people started sharing photos of Unite the Right on the Internet in order to "crowdsource" identifying members of the groups. Results came rapidly. One marcher from Berkeley, California, lost his job at a hot dog restaurant as a result of being identified, as complaints poured in from customers. Another from Fargo, North Dakota, was disowned by his family. One person posted to the now-offline Daily Stormer that he would not attend future rallies because "the thought of getting outed as 'white supremacists' to our employers and possibly losing our jobs is a horrifying prospect," as Steve Blum reported in Broadly.
Many of the identifications have been coordinated through a Twitter account called Yes You're Racist.
If you recognize any of the Nazis marching in #Charlottesville, send me their names/profiles and I'll make them famous #GoodNightAltRight pic.twitter.com/2tA9xliFVU
— Yes, You're Racist (@YesYoureRacist) August 12, 2017
There have been misfires. As The New York Times reported, Kyle Quinn—an assistant professor at the University of Arkansas' School of Engineering—was misidentified as a marcher, resulting in a torrent of threatening social media messages.
But that's just the start of a growing online campaign mounted by members of an Anonymous collaboration called OpDomesticTerrorism and others. With sites like the Daily Stormer being driven offline and having their social media accounts suspended, Andrew "weev" Auernheimer warned followers of his Gab account that they might become targets of phishing attacks using lookalike social media accounts.
"The Daily Stormer status account on Twitter got suspended," he wrote. "There are some impersonating accounts made now. Don't click on any links they give."
Daily Stormer moved to a Tor hidden service this week after GoDaddy pulled the site's domain name.
We informed The Daily Stormer that they have 24 hours to move the domain to another provider, as they have violated our terms of service.
— GoDaddy (@GoDaddy) August 14, 2017
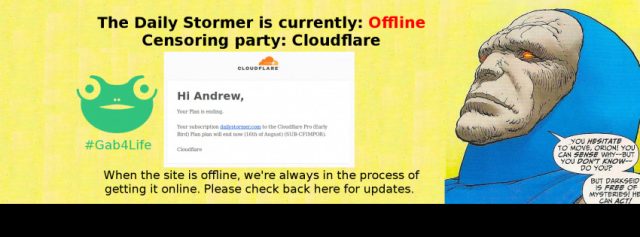
Today, the site was back up with a Russian domain, but within just two and a half hours it was down again when Cloudflare canceled the site's service. Andrew Anglin, the man behind Daily Stormer, posted an image of Cloudflare's cancellation of his account on his Gab feed. So, as of this afternoon, Anglin and Auernheimer were scrambling to restore the site on Tor while they looked at another way to host the site that would protect it from attacks.
The Tor site may come under attack as well. Currently, the placeholder page for the "dark web" version of the site is a hand-encoded HTML page that doesn't betray much about the system it is hosted on. But a hacker claiming to be involved in the Anonymous operation told Ars that they were attempting to launch a denial-of-service attack over Tor on the Daily Stormer's .onion hidden service.
Additionally, the Stormer's Web discussion board, which was hosted on a service based in Belize, was taken offline after being exposed by attackers.
Dear Anonymous..https://t.co/Jqfd3yv77l - http://91.209.70.50#Exposed#OpDomesticTerrorism#Anonymous#Charlottesvillepic.twitter.com/Ac3oD2IBJ3
— New World Hackers (@nwhownz) August 15, 2017
IRC discussions among Stormer supporters also were targeted:
Yesterday night #DailyStormer gathered in an irc server to discuss the makings of a .onion website. https://t.co/cpvDRJ2jWa#offline#OpDTpic.twitter.com/CNaS4dDQu2
— New World Hackers (@nwhownz) August 16, 2017
The group contacting Ars has previously claimed responsibility for setting off warning sirens in Dallas, which could not be verified, and has made other dubious claims in the past. But these details appear genuine.
reader comments
407